Quarterly (and annual) threat reports drive leads and build trust as thought leaders share their insights on currently emerging cyber threats.
But how do you report on what you find, reach your audience, and cut through the noise?
Writing about cybersecurity threats is often one of the first ways that cybersecurity challenger brands get attention from potential customers. It allows them to capitalize on timeliness and intense interest to circumvent the near monopoly that established players in this space have over search results and news channels.
Threat reporting can serve as a launch pad for content dominance, leading to increased domain authority and greater exposure for other content. Eventually, teams start to ask how they can parlay their best-performing content into a more robust threat report, published periodically.
The issue?
Everyone seems to have a quarterly or annual cybersecurity report.
And even after gaining some momentum from periodic newsworthy pieces on new threats or threat-hunting findings, content leaders may still find they don’t have the secret formula for packaging institutional knowledge about cyber threats into reports that people want to read.
In this article, we’re breaking down today’s top-ranking reports in Google, explaining why they’re doing well, what commonalities they share, and where to change tactics, in order to make your own cybersecurity report gain ground in 2025.
The bottom line? The top-ranking cybersecurity reports are from established companies with authority and backlinks profiles a mile long. Challengers won’t rank on this lucrative bottom-of-the-funnel (BOFU) play, so they’ll have to get creative.
Methodology
We looked at the top cybersecurity threat reports topping Google’s searches in June 2025, logging SEO insight like:
- The ranking sites’ domain authority
- The rank of the site’s backlink profile
- The total number of backlinks to the domain
- The total number of backlinks to the unique URL
- The estimated monthly search traffic to the specific page
- The word count of the specific page
In addition to these quantitative measures, we mined the top 5 ranking reports themselves (omitting those from government agencies and instead focusing on commercial threat reports against which new brands might compete):
1. CrowdStrike’s Global Threat Report
2. Fortinet’s Threat Landscape Report
3. Checkpoint’s Cyber Security Report 2025
4. NCC Group’s Cyber Threat Intelligence Report
5. TrendMicro’s Cybersecurity Threat Report
(We omitted two otherwise ranking Cisco pages to report download landing sites where no single report was a general, periodic cybersecurity threat report.)
While this tiny sample size cannot give us definitive conclusions, it can offer a glimpse into the most popular formats, missing pieces, and common site statistics.
So – we wanted to see:
- What topics did they cover – to help with your ideation.
- Do you have to fill out a form to see the content? There’s mixed opinion on whether you should gat content or let it fly freely for the SEO + AI bots
- How do you plan the creation of the lead-gen asset?
- What are some killer themes + framework examples from top leaders that you can learn from, so that you can deploy to create your own – fast.
Cybersecurity Report Examples: Top 5 Heavy-Hitters to Learn from
First, to set the stage, here are 5 example cybersecurity reports we love to hold up as well-done assets to learn from:
1. CrowdStrike’s Global Threat Report
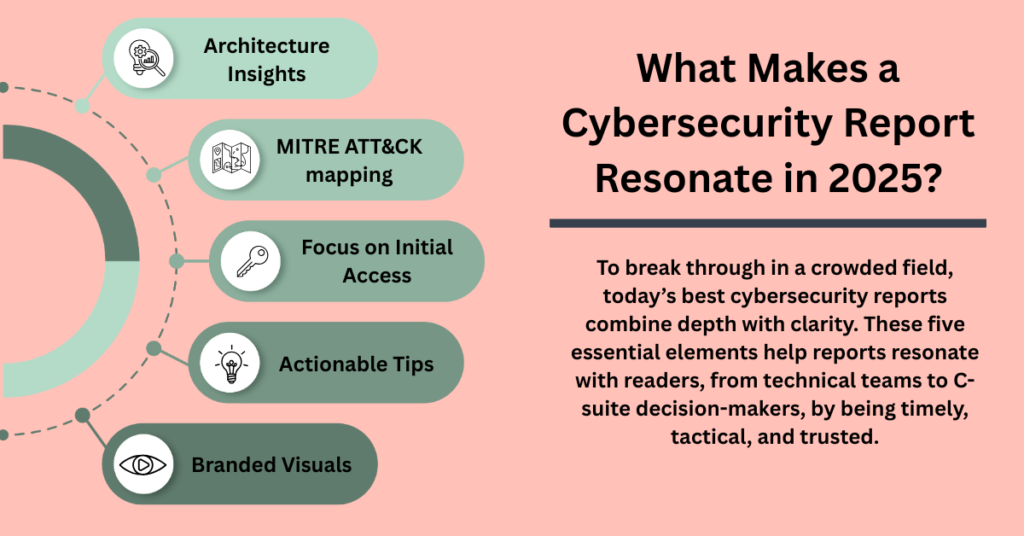
- Emphasis on Initial Access: Highlights that 52% of observed vulnerabilities in 2024 were related to initial access, underscoring the importance of early detection and prevention
- MITRE ATT&CK Framework Alignment: Provides comprehensive analysis of attack tactics based on the MITRE ATT&CK framework, facilitating a common language for understanding threats.
- Focus on Dominant Trends: Details a 442% growth in vishing operations and a 150% increase in China-nexus activity, reflecting the evolving threat landscape
- Branded Visuals: Utilizes clear charts and graphs to make complex data more accessible and skimmable.
- Actionable Insights: Offers anticipatory threat assessments to help organizations prepare and protect against emerging threats.
2. Fortinet’s Threat Landscape Report
- Information on Architecture: Discusses the challenges organizations face with accelerated reconnaissance and widespread exploitation, emphasizing the need for modern defense strategies
- Focus on Initial Access: Highlights a surge in credential theft, pointing to the critical nature of securing initial access points.
- MITRE ATT&CK Framework Alignment: Provides in-depth analysis of attack tactics based on the MITRE ATT&CK framework.
- Focus on Dominant Trends: Reveals a dramatic escalation in both the scale and sophistication of cybersattacks, with adversaries leveraging automation and AI.
- Branded Visuals: Includes detailed charts and timelines to illustrate the evolving threat landscape.
- Actionable Insights: Recommends adopting AI, zero trust architectures, and real-time threat management to counter sophisticated cyberattacks.
3. Checkpoint’s Cyber Security Report 2025
- Information on Architecture: Addresses increased targeting of edge devices and new threats against cloud environments.
- Focus on Initial Access: Reports a 58% rise in infostealer attacks, emphasizing the need to secure initial access vectors.
- MITRE ATT&CK Framework Alignment: By mapping observed attacks to the ATT&CK framework, the report helps organizations understand attack patterns, identify potential vulnerabilities, and prioritize their defenses.
- Focus on Dominant Trends: Highlights the increasing role of generative AI in cyber attacks and a 44% rise in global cyberattacks.
- Branded Visuals: Presents data through clear visuals to aid understanding of complex threats.
- Actionable Insights: Provides practical advice for CISOs to navigate the evolving cyber threat landscape.
4. NCC Group’s Cyber Threat Intelligence Report
- Information on Architecture: Offers insights to emerging trends by region and sector, including a focus on supply chain security
- Focus on Initial Access: Provides monthly trend spikes and tactical observations, aiding in early detection of new attack methods.
- MITRE ATT&CK Framework Alignment: Includes this framework into their cyber threat intelligence reporting and aims to deliver actionable insights that enable organizations to better understand, prioritize and defend against evolving threats.
- Focus on Dominant Trends: Explores the impact of AI and generative technology on cyber threats, including the rise of AI-enabled crime.
- Branded Visuals: Utilizes visuals to highlight key findings and trends.
- Actionable Insights: Provides insights into new threat actors and the most impactful active cyber threats, aiding organizations in proactive defense.
5. TrendMicro’s Cybersecurity Threat Report
- Information on Architecture: Analyzes exposures and attacker behavior to implement countermeasures, transforming security into a business enabler.
- Focus on Initial Access: Emphasizes the importance of staying ahead of threats by recognizing exposures and understanding attacker behavior.
- MITRE ATT&CK Framework Alignment: Leverages the MITRE ATT&CK framework to provide a structured approach to understanding, detecting and responding to cyber threats, enabling organizations to enhance their security posture and mitigate risks effectively.
- Focus on Dominant Trends: Highlights the role of AI in intensifying cyber threats and the importance of proactive security measures.
- Branded Visuals: Includes visuals to illustrate the Cyber Risk Index and other key metrics.
- Actionable Insights: Provides insights into reducing cyber risk scorwes through proactive security measures.
By the Numbers: What the SEO Data Tells Us
Unsurprisingly, there’s high competition for eyeballs when it comes to cyber threat reports.
With an average domain authority of 86.8 across the top ten results, ranking reports are likely originating from tech giants and long-established publishers. And when it comes to backlink strength, the average ranking of the top ten Google results is in the top .01% globally for all websites.
Overall, Google is serving results that are dominated by some of the most authoritative sites on the internet. That’s only reinforced by the average total domain backlinks (163+ million) and page-specific backlinks (Over 7,300).
Newcomers hoping to compete here would need ongoing, strong link-building campaigns and in-depth, optimized content to rank, even well down the leaderboard.
Breaking it Down Site by Site
When it comes to word count, the top-ranking pages average more than 1,500 words each, indicative of comprehensive content, even though every one of our commercially produced reports was gated.
In fact, even government site reports weren’t simply located on ranked pages. The U.S.’s Cybersecurity and Infrastructure Security Agency (CISA) ranks 2 pages in the top ten for “cybersecurity threat reports”: its Cyber Threats and Advisories landing page and its latest Cybersecurity Alerts and Advisories. What’s the difference? The first is a topic hub, linking to the second. The second is a chronology of the latest events; it’s the closest thing this field of Google results has to a blow-by-blow of news-worthy cyber threat reporting.
When it comes to quarterly or annual reports (plus one biannual report), the rest of the field is primarily concerned with consolidating newsworthy reports, rather than the chronologies themselves.
What about the commercial reports, once downloaded? They average a beefy 13,840 words. The shortest are monthly or targeted analyses (NCC and Fortinet), while the longest, topping 23K words, are annual reports and retrospectives with deep analyses.
What to Do When Creating a Cybersecurity Threat Report
The good news for challenger brands is that BOFU content has never been an ideal SEO play. While CISA’s pages attract thousands of visitors per month, others win as few as 30 from all keywords. The solution? Throw ranking ambitions out the window and focus on using a cyber threat report to attract a new audience using alternatives to SEO.
- Stand out with niche strategic intent when you can’t harness sheer SEO power, and stop aiming to dominate the titans. Big vendors tend to focus on high-level, global metrics and generalized advice for other large organizations. But those who can go deep on a niche (like multifactor authentication bypass techniques or Mac malware in creative industries, for example) are positioned better to get in front of those who are ignored by most threat intel.
- Try out-formatting the big players. Earn loyal readers by being more useful when you can’t be more authoritative. Going deeper into a niche is one way. Another is to consider building an interactive microsite instead of a templated .pdf or slides. Include scrollable timelines, filterable data on threat types, and other user-friendly accents. Format can help differentiate organizations as much as findings can.
- Use your unique voice. Engage the data and knowledge you have rather than repeating generic storylines. Detail where your pipeline failed to catch a data breach. Share “how we caught it” stories. Share results and analyze problems with transparency. And don’t forget to include a clear editorial tone, including editorial hot-takes from your subject matter experts that help explain why you do things differently.
This may be the point where you ask, “Yeah, but how do we get these clever and specific reports in front of anyone if we give up on ranking?”
First, you’re not giving up on ranking. You’re giving up on ranking in the top ten for cybersecurity threat reports for now, and while you grow the authority it takes to rank there. You’re using your threat reports to grow that authority, audience, and linkability. When Red Canary was small, they dominated detection and response for small and mid-market organizations, writing about failures in an accessible way that the big players couldn’t imitate. Consider a similar angle in your own niche.
Second, use the tools of smaller companies to make inroads against bigger competitors. Consider how speed and smallness are advantages. Try distributing your unique report in bite-sized ways, customized for different audience verticals or regions: LinkedIn carousels, one-pagers, 5-minute reads for CISOs newsletters, and conference talks.
Ultimately, engage readers on the specifics more so than large players can. If someone bookmarks one page of your report to revisit, you’re winning. After all, annual reports are a bottom-of-the-funnel and authority-building tool, not a traffic driver.
Learning from Threat Report Content
In the reports themselves, consider some common must-haves that these competitors nevertheless include across the top ten:
- Information on architecture: It’s hard to address threats without addressing the underlying reality of cloud, SaaS, and hybrid environments, and the prominence of issues like identity in breaches and lateral movement.
- A focus on initial access: Early-stage tactics keep threat reports zoomed in on new attack methods and earlier detection and response — as well as prevention.
- Common ground with the MITRE ATT&CK framework: Reports wholly reference MITRE, which creates a common language for understanding techniques and threats.
- Sections addressing dominant trends: In this year’s reports, it’s difficult to escape timely data on the skyrocketing use of AI and automation to wage attacks.
- Branded visuals: Charts, graphs, and timelines make reports skimmable and aligned to the vendor’s branding.
- Actionable tips: From detection to response recommendations, the reports suggest new ways to proactively address new threats.
As readers move through key sections on tactics and architecture, they’re led to big trends, then actions they can take to prevent and address them. It’s a standard narrative, and it’s effective in that it contextualizes the year’s threats and empowers readers to take action.
But in a crowded field, addressing these must-haves won’t help newcomers rank. Even among large reports, it’s evident that “standing out” is as important as fitting in. And even big players take a unique angle on these threat reports. For example:
- Focus Areas: Overall, all reports address unique vendor positioning. Fortinet focuses heavily on automated reconnaissance at the network edge (aligned with Fortinet’s scanning and edge infrastructure). Red Canary emphasizes detection that bypasses customer controls, hammering home the theme of catching what other tools miss.
- Specificity: All reports are reasonably general, but Check Point comes with the broadest scope: geopolitics, malware, cloud, and edge computing mix for higher-level reflections and market-level insights.
- Timeliness: NCC brings trendiness to another level, with monthly trend spikes and tactical observations.
- Naming Conventions: Multiple reports use signature naming to associate their brand with threat detection. Red Canary uses colorful birds, for instance, while CrowdStrike’s report uses animals to represent countries and fields (i.e., pandas for Chinese actors and spiders for financially motivated crime).
- Tone: Different audiences are suggested by Fortinet’s formal, analytical voice, while Red Canary takes a conversational and tactical approach.
- Data Sources: CrowdStrike heavily emphasizes threat hunting telemetry and tracking nation-state actors. Red Canary discusses MDR visibility (detecting threats other tools don’t).
- Industry Alignment: Some reports have an industry-agnostic approach, while others have a strong focus on areas like government, aerospace and defense, healthcare, or financial sectors.
What’s Missing? New Voices
Despite their breadth and polish, the five major reports still leave plenty of gaps. These omissions create room for newcomers to find a voice. And if that’s not in the top ten Google results, it’s certainly in other venues where audiences reside.
Practitioner How-To
Most reports stop short of helping detection engineers. They’re built for CISOs and don’t translate well into actionable defense in a detailed way. What to do? Try offering threat emulation guides, updated for annual threat developments. Share detection engineering examples. Map playbooks to real TTPs.
Security Layer Differentiation
CrowdStrike owns endpoint and identity. Fortinet owns the perimeter. Red Canary covers MDR… but that’s not everything. Consider addressing SaaS app security, API abuse, CI/CD pipeline, or end-user behavior.
We’ve helped differentiated newcomers carve out their area, and the benefits reach beyond the annual report — they lead to more middle-of-the-funnel SEO wins around stack layers that few other competitors are addressing, for an SEO foothold into more generic keywords and terms later.
SMB Lens
Small and medium businesses can fall through the cracks, with most advice aimed at enterprises. Offer threat modeling, tooling guidance, and prioritization frameworks all along the growth curve, helping SMBs know when and why to upgrade security and how to navigate these same threats with fewer resources.
New Regions
Emerging markets are also left out of most threat reports. Use breach data, Telegram channels, or local intel feeds to talk about these differences and create defenses that are specific to a region and its threat actors.
AI Threats
One top ten report page contains no annual report on broad cybersecurity and threats, but it does contain proprietary reports on AI, suggesting reports like this have become heavy hitters in the world of cybersecurity reporting. But they seldom get their own spotlight. Consider a security area like GenAI, covering the topic thoroughly rather than including it in a larger, more generalized report. Ake AI-native threats a core research focus, and go deeper than the competition.
How Smaller Players Can Set Up Bigger Plays
In a world of KPIs, stakeholders can get fixated on making the annual report rank. But it’s not about the anonymous 30 visitors that Google sends to sites (and only then, after years of sophisticated marketing work). It’s about creating authority: among casual LinkedIn readers, potential podcast hosts, and even Google, though not in the way most stakeholders would imagine.
If not ranking plays, annual reports are still a definitive, authoritative link and lead magnets that can differentiate challengers from those big, general brands that move slowly and try to speak to everyone in the room. Annual reports are branding. They’re sales. They’re PR. And they’re related to your SEO efforts. But where they land in the search results shouldn’t be their endgame.
Instead, use your annual report to dive deeper, smaller, and faster into areas where others don’t tread.
Just don’t pay too much attention to your Google ranking along the way.







Leave a Reply